Risk assessments are one of the most important parts of an organisation’s ISO 27001 implementation project. The process can be tricky, but we’ve simplified it in this blog by breaking it down into five easy-to-follow steps. Establish a risk management framework. The risk management framework governs how you identify and manage risks. Answer: ISO 27001 does not prescribe a methodology, only that one must be defined and documented, so you can adopt the methodology that best suits your needs. The asset-based risk assessment is includ ed in the toolkit because it is the most common approach used for information security risk assessment, and this is also the one that provides.
Assign topic to the user
Please select user.
ISO 27001 DOCUMENTATION TOOLKIT
Step-by-step implementation for smaller companies.
Find out more
ISO 27001 DOCUMENTATION TOOLKIT
Step-by-step implementation for smaller companies.
ISO 27001 DOCUMENTATION TOOLKIT
Step-by-step implementation for smaller companies.

Answer: ISO management standards do not prescribe how to implement risk register, so both approaches are acceptable. A single risk register can show you a systemic view of all risks the organization is exposed to, but it is also more complex to analyze. A risk register for each aspect helps you focus on relevant risks for each aspect, but it will require more administrative effort to maintain. You have to evaluate these situations to identify which approach is better for your organization.
2. I also see that the risk assessment that came with the pack is asset based risk assessment.... is that mandatory?
Answer: ISO 27001 does not prescribe a methodology, only that one must be defined and documented, so you can adopt the methodology that best suits your needs. The asset-based risk assessment is includ ed in the toolkit because it is the most common approach used for information security risk assessment, and this is also the one that provides the best balance between precision and needed effort.
This article will provide you further explanation about risk assessment:
- ISO 31010: What to use instead of the asset-based approach for ISO 27001 risk identification https://advisera.com/27001academy/blog/2016/04/04/iso-31010-what-to-use-instead-of-the-asset-based-approach-for-iso-27001-risk-identification/
Jun 12, 2019
ISO 27001 is the most popular information security standard worldwide, and organisations that have achieved compliance with the Standard can use it to prove that they are serious about the information they handle and use.
ISO 27001 is the globally accepted standard that offers clients the assurance that the organisation is managing the confidentiality, integrity and availability of information.
Iso 27001 Risk Register Download
One of the cornerstones of implementing an ISO 27001-compliant ISMS (information security management system) is conducting an effective information security risk assessment.
Mitigate your risks
Iso 27001 Risk Assessment
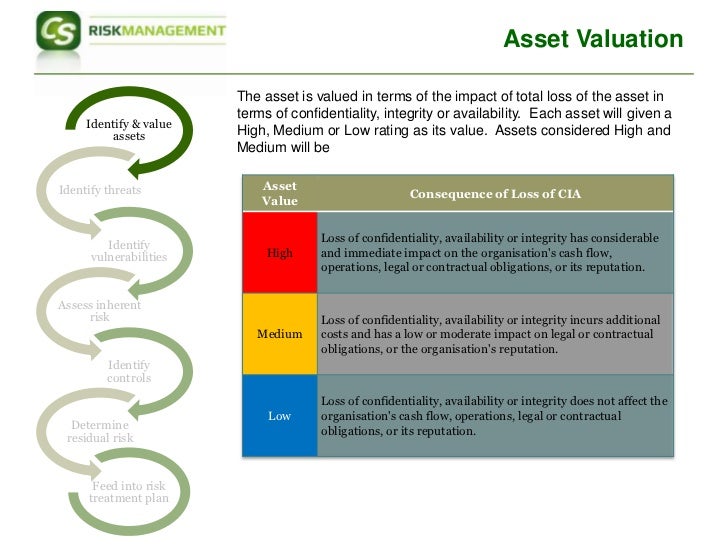
In order to tackle the risks to your organisation’s information assets, the assessor will usually need to take the following broad steps:
- Identify the various information assets that could be jeopardised.
- Consider the threats that could compromise those assets.
- Assess the vulnerabilities in the organisation that could compound those threats.
- Establish the likelihood and impact of such risks coming to pass.
- Estimate the damage that such threats could bring about.
Once this part of the risk assessment has been completed, the next critical element is to identify and select the relevant controls from Annex A of ISO 27001:2013 (or elsewhere), to ensure that each of the risks has been treated effectively.

Risk management
The organisation may choose to treat, tolerate, transfer or terminate the risk, based on the company’s risk appetite and the total estimation of the risk.
There are, of course, a number of other things that need to be considered throughout the process, such as what the organisation’s risk appetite is, what kind of risk assessment criteria to use, in addition to what risk calculation formula and additional sets of controls to apply.
The easiest way to get this done is with risk assessment template.
With a template, there is no need to compile extensive lists of assets, no need to try and find a library of threats and vulnerabilities (or risks), no need to wonder which threats could affect which assets, and no need to try and think which controls would apply to which risks. With vsRisk™, all of this has already been done for you.
With vsRisk, you can copy, edit and replicate a built-in risk assessment template, populated with the following:
- A library of assets, pre-assigned to organisational roles that typically manage those assets;
- Pre-selected threats and vulnerabilities (risks), applied to each asset group;
- The relevant ISO 27001:2013 controls pre-applied to each risk.
In addition, vsRisk features customisable and editable reports, such the SoA (Statement of Applicability) and Risk Treatment Plan, which are crucial for an ISO 27001 audit.
Looking for more compliance advice?
You can find out more about identifying and evaluating your interested parties with the help of CyberComply.
This Cloud-based collection of information security software helps you take control of your cyber risk needs in one simple package.
Iso 27001 Risk Register
It includes a feature that identifies the relevant legal, contractual and regulatory obligations you need to meet to ensure compliance with the interested parties clause of ISO 27001.
Iso 27001 Risk Assessment Template
A version of this blog was originally published on 18 July 2016.
